To some, the cyber insurance policy may appear to be quite a complex offering, but to those engaged in the Cyber Insurance arena, this is an exciting and challenging time. I believe that in the coming years, this unique product will become a “must” in every insurance program offered around the world.
The cyberspace is no longer the sole playground for hackers, programmers, and engineers, as online communication platforms have become essential too. Organizations are more dependent than ever on technology and connectivity and are finally understanding that virtual risks are becoming more important than physical risks.
Cybercriminals remain one step ahead and many companies have already experienced harmful cyberattacks. And yet, the existing knowledge amongst insurance professionals remains far behind. This knowledge gap eventually affects the ability of insurance personnel to sell cyber insurance and weakens their ability to assist their clients in transferring the cyber risk to the insurance company.
A prosperous future for the insurance industry can only be reached through innovation. But innovation will always bring challenges. Now is the time to take active steps to identify, educate and tackle these challenges head-on.
During this article, I’ll focus on what makes the Cyber Insurance Policy such a unique product, but before I do so, let me explain what exactly Cyber Insurance is using a simple metaphor:
Take your house, for example. It doesn’t matter if it’s an apartment in a city or a larger house in the suburbs, you would try to keep it as safe as possible. All of your personal and most important belongings are there, including things you spent a lifetime gathering. So, you would install a large steel door that can only be opened with a unique key, you may install a fence that is as tall as possible, together with security cameras and a top alarm system. You may even bring an intimidating guard dog that would do its best to deter potential burglars.

You can invest millions in countermeasures, but still, your house wouldn’t be 100% protected, there is always some chance that it would be breached. In other words, there is always a residual risk. And what do you do in order to mitigate this remaining risk? You buy an insurance policy.
The same goes for cyber risks. You can install a firewall, or antivirus, require a finger scan to log in, and all other solutions, technical and advanced as they may be, and still, there is a potential to be hacked. Again, no matter how many countermeasures you have, there is still a residual risk. Digital risk is inherent in almost every activity a company undertakes and is hardly avoidable.
This risk, once again, can be mitigated by purchasing a cyber insurance policy.
However, it is not that simple, it is not like other traditional policies; the cyber liability policy is unique and distinctive, it has elements and challenges that can only be found when talking about the risk of cyber. At the moment, it’s important to understand that cyber insurance is not a replacement for security practices, rather, it is complementary and is an inseparable part of any company’s robust security posture.
Now, after clarifying what cyber insurance is by comparing it to more traditional risks, I will describe the different elements that make the cyber policy so unique.
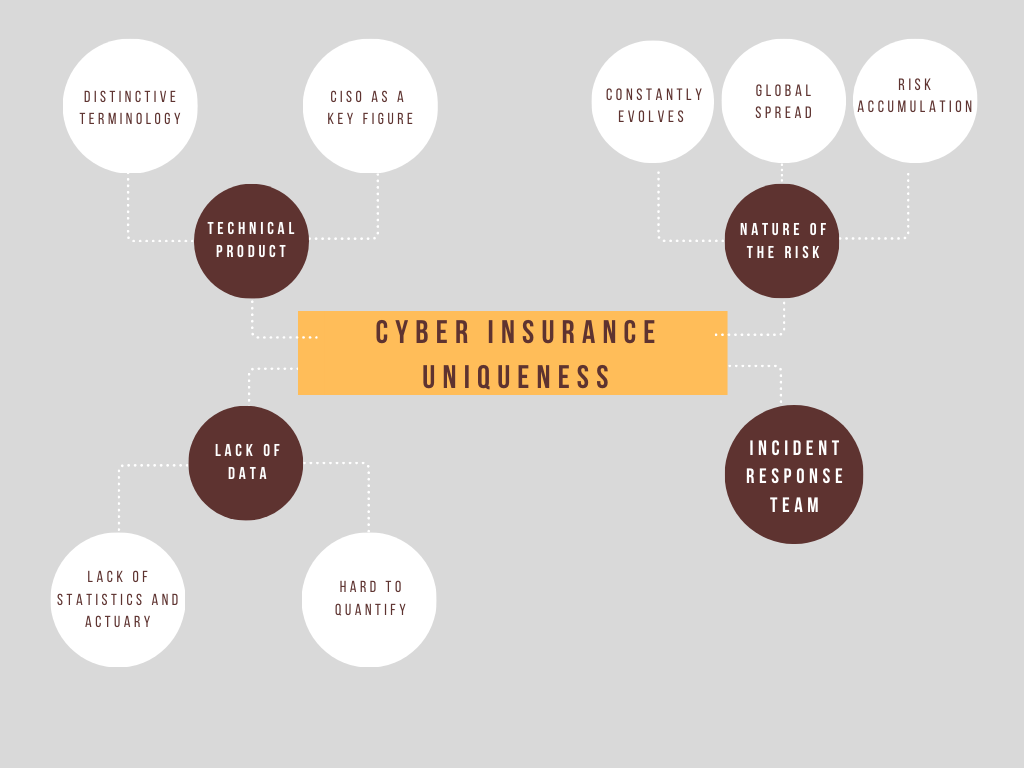
The Cyber Insurance Policy is a Technical Product
Distinctive Terminology
Most traditional insurance products are addressing well-known topics which are part of our daily lives. Insurance professionals are well acquainted with these matters.
When it comes to cyber, most insurance professionals do not have the required fundamental terminology and understanding of the new and emerging cyber risks, and as a result, they often shy away from dealing with them.
As professionals managing risks for clients, we must have all the available knowledge and necessary tools in order to tailor the best solution.
CISO as a Key Figure
Most of the discussion on other insurance products is conducted in front of the CEO, COO, CFO, or risk managers. When it comes to Cyber Insurance, the discussion is very technical and is mainly conducted in front of cyber security and IT professionals.
A Cyber Insurance professional who is not familiar with the “cyber language” won’t be able to conduct a productive meeting with the CISO/CIO.
This gap affects the ability of insurance professionals to converse with potential buyers of the Cyber Insurance product, and, as a result, they will most probably not convey the right message and may even miss the opportunity to materialize a sale.
Lack of Data on the Cyber Insurance Policy
Lack of Statistics and Actuary
Insurance products are based on past experience, accumulation of data, statistics, and actuarial findings. This data is the basis of the pricing model and sets the level of coverage provided by insurance companies.
When it comes to the Cyber Insurance product, which is still a very “young” product, all the above necessary information is still largely unavailable, making the product quite unique.
The lack of knowledge and data makes underwriting cyber risks much more complicated and therefore susceptible to underwriting mistakes. This has led underwriters to approach cyber risks cautiously thus far.
Hard to Quantify Risk for Cyber Insurance Policy Underwriting
Cyber security is a boardroom issue, and as such, it needs to be addressed accordingly. The risk should be measured and reported in financial terms, allowing C-level executives and board members to know more about the risk and make more educated decisions.
Unfortunately, when it comes to the field of cyber, traditional methods of risk measurement don’t provide sufficient insights anymore.
First, as mentioned, there is a shortage of contextual data on cyber incidents to feed the quantitative risk calculator, and second, there is a false perception that cyber risk is complicated and should be “left” with the technical people to deal with.
Quantifying the risk has many diverse aspects which are not solely technical. I shall use an example to clarify; In order to assess potential damage from data leakage, one needs to evaluate the amount of data (PII, PHI, PFI) and the geographical spread of such an event. The cost may vary dramatically if the exposure takes place in one country or another.
New technologies are emerging to assist in the quantification process, and, as we progress with time, we are likely to see more and more advanced and innovative technologies coming into this arena.
The Changing Nature of the Risk and how that is reflected in Cyber Policies
Constant Evolution
Cyber risk is an ever-changing one. The accelerated technological development in the business environment constantly creates new cyber threats. These new and emerging threats may impact businesses at different levels of severity and must therefore be evaluated constantly.
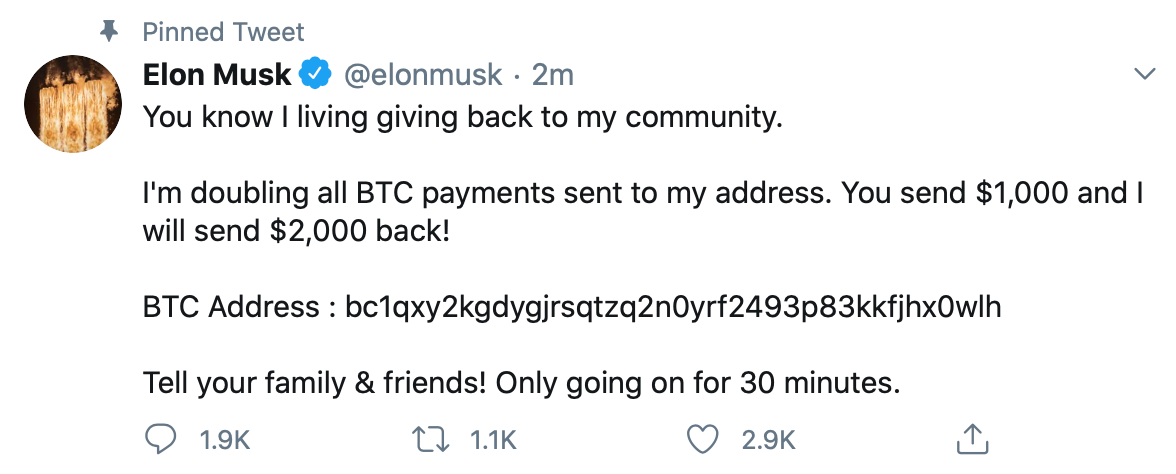
It was only recently that we saw Twitter, a mega-corporation, being hacked, and for reasons that are not obvious. The following tweet was posted on several accounts, including; Barack Obama, Joe Biden, Bill Gates, and Elon Musk. The tweet said “I am giving back to the community. All Bitcoin sent to the address below will be sent back double! If you send $1,000, I will send back $2,000. Tell your family & friends! Only going on for 30 minutes.”
This high-profile incident was a result of something called a “coordinated social engineering attack” which led to the compromise of a group of employee credentials. Two of the many attackers claimed that they bribed a Twitter employee for access to the control panel.
Global Spread
Man-made catastrophes such as terrorist attacks and natural catastrophes such as hurricanes or earthquakes are usually limited geographically. On the other hand, Cyber Space has no geographical boundaries. The WannaCry and NotPetya events have demonstrated that cyber is a global threat with the potential to spread.
The WannaCry outbreak in 2017 demonstrated the impact of an infrastructure attack on public service. This attack had widespread consequences; around 200,000 computers were infected across 150 countries.
The NotPetya cyber event in 2017 started as a state-sponsored attack between Russia and Ukraine. However, the malware, in a matter of hours, traveled all around the globe, affecting thousands of businesses, including global corporations such as Maersk, the largest shipping company in the world, the logistics giant FedEx, and the pharmaceutical conglomerate Merck.
Risk Accumulation
Cloud computing, and other outsourced services, are concentrated among large global providers, such as; AWS, Azure, Google, Salesforce, etc. The ever-growing need for availability and storage space has given rise to the use of cloud computing and shared resources.

However, this has also exposed companies to new vulnerabilities and dependencies on the availability of these cloud providers. The probability of a top cloud service provider suffering from complete unavailability is low, but, if realized, it would have a catastrophic impact on the global economy.
Incident Response Team (IRT): a novel concept to the cyber insurance policy
As the threat of cyber incidents grows, and the impact of such threats has a global reach, insurance companies are increasingly partnering with third-party “breach response services” to provide a local and international offering to mitigate the potential impact of a cyber incident. In most cyber insurance policies, such services are built into the policy.
When dealing with cyber incidents, a quick and professional response can determine the severity of the damage of the incident. In order to mitigate the impact successfully, the policy provides a unique offering in the form of a technical, legal, and PR panel of local and international vendors.
Insurers’ approaches to breach response differ; some insurers specifically point out their preferred vendor, and some are open to adding additional vendors named by the insured. Some have one large IRT that deals with everything, and some are made of multiple vendors, each specializing in their own field. Some keep it in-house, and some use third parties.
There is no one formula for IRT!
The global Coronavirus crisis presented an opportunity for the cyber industry and specifically for the Cyber Insurance industry. Many businesses and governments were forced to progress and implement many new and rapidly changing technological solutions.
Progress and innovation are important, but they also bring new security risks and new types of attacks, and eventually, this leads to increased product awareness with companies seeking to transfer the risk to the insurance company.
The cyber insurance policy offers this protection. It is the future, but the future is already here.
Interested to learn more about the latest developments in cyber insurance? Visit our course catalog for more information on our cyber insurance training.








