As the world becomes increasingly interconnected and digital, cyber security has become an ever more pressing concern for businesses and individuals alike. In a recent Masterclass led by Zscaler, experts Kavitha Mariappan and Stephen Singh discussed the evolution of cyber security over the years and how this has led to the development of the zero trust framework, a new approach to securing digital systems and data. This article summarizes their key points, and, in particular, explores how Zero Trust came to represent the intersection of cyber Insurance underwriting and the cyber security industry.
The Impact Of Technological Advancement On Today’s Cyber Security Management Techniques
Kavitha kicked off the Masterclass by discussing the intersectionality of zero trust security and cyber insurance underwriting in the rapidly evolving technological landscape of the past decade. For example, the transition of data center virtualization and the move to cloud-based applications and workloads, the evolution of worker and user mobility, and the proliferation of devices that can access critical data – each has contributed to the rise of the zero trust framework. Technological change has also required businesses to think differently about how they operate, structure their organizations, and protect themselves from threats and regulations. Without continuous innovation and technological evolution, most organizations have been unable to remain profitable and secure.
A Brief History Of Cyber Security Transformation
Kavitha then moved on to examine the evolution of cybersecurity over the past few decades from a locked-in approach, where organizations focused on securing their perimeter with routable networks, hardware, and complex security implementations, to the current environment where data is no longer restricted to the organization’s four walls, users are mobile and utilize multiple devices, and applications have moved to the cloud.
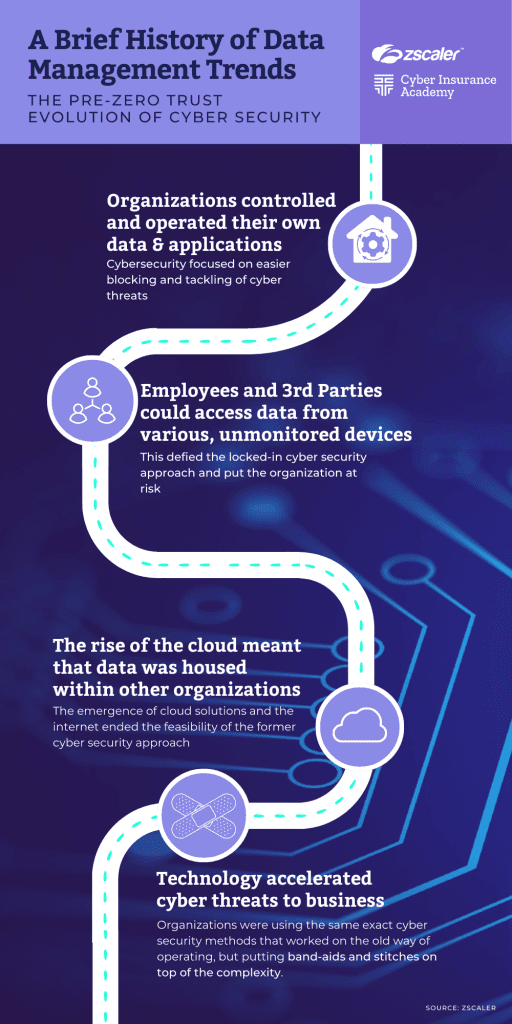
This new environment presents challenges for organizations as they need to secure critical data, protect users, and enhance workplace productivity. The legacy implementation of cybersecurity, which focuses on securing the perimeter, is no longer sufficient for this new world. CISOs have therefore needed to think about a new topology that lends itself to this new way of accessing and delivering data while providing enhanced user experience and productivity. Rather than extending the physical corporate perimeter to the edge, organizations need to rethink their cybersecurity paradigm.
Increasing Attack Surfaces & the Rise of Zero Trust
Increased reliance on cloud technology has resulted in a larger attack surface for cyber threat actors, whether internal, external or state-sponsors. Kavitha warned that the cost, frequency, and severity of cyber attacks are outstripping the industry’s ability to insure every organization, and that the impact of these attacks can extend beyond the loss of data to endangering critical infrastructure and citizen safety. For that reason, organizations have begun to prioritize cybersecurity measures and take proactive steps to protect their assets and customers. Recent years have brought a shift in focus towards identity management, behavior analysis, and posture assessment, and the importance of building safeguards to prevent and mitigate cyber attacks.
That’s where Zero Trust security comes into the picture as a way of making the attack surface near-invisible to nefarious actors. Zero Trust security is not a single product or solution, but rather an industry leading strategy that can be applied by companies of all sizes and that requires an ecosystem that focuses on policy management, identity, and endpoint management. The movement towards this framework is gaining momentum globally, and it has become a standard for cybersecurity objectives in the United States federal government and agencies. It focuses on obfuscating the attack surface, preventing lateral transition, and adding elements of identity and access management.
Why Insurance Professionals Should Care About Zero Trust Frameworks
Zero Trust Defined
The key elements of a Zero Trust framework include:
- Never trust, always verify
- Give access only as needed
- Always confirm who the user is, what information they are trying to access, what minimal privilege they have to see it
- Prevent access to ‘the crown jewels’ of the organization
- Block internal movement of any individual through an organization’s data
- Eliminate the attackable surface of the organization
You can read our guide on “Zero Trust In 4 Steps” to understand how your insureds should be putting this framework into practice.
Zero Trust and Risk Management for Cyber Insurance
Stephen noted that, while the cyber insurance industry has been managing cyber risk increasingly well,
“Zero Trust provides an elevated level of hygiene that can help to mitigate these risks even more effectively and improve underwriting. It can be used in collaboration with cyber insurance providers to identify coverage and potential financial loss.”
He emphasized that zero trust is not just a niche approach, but the new merging standard to identify risks, threats, and vulnerabilities.
Benefits of Zero Trust For Cyber Insurers
Stephen explained how and why, for cyber insurance providers, zero trust offers a comprehensive and transparent view of the entire IT estate, enabling them to better understand the level of risk and potential financial loss associated with a cyber incident. By combining an inside-out zero trust approach with outside-in techniques, insurers can gain a 360-degree view of the security landscape, and create policies that are both granular and automated. Zero trust also enables insurers to predict and prevent cyber incidents, and to rapidly mitigate threats, risks, and vulnerabilities.
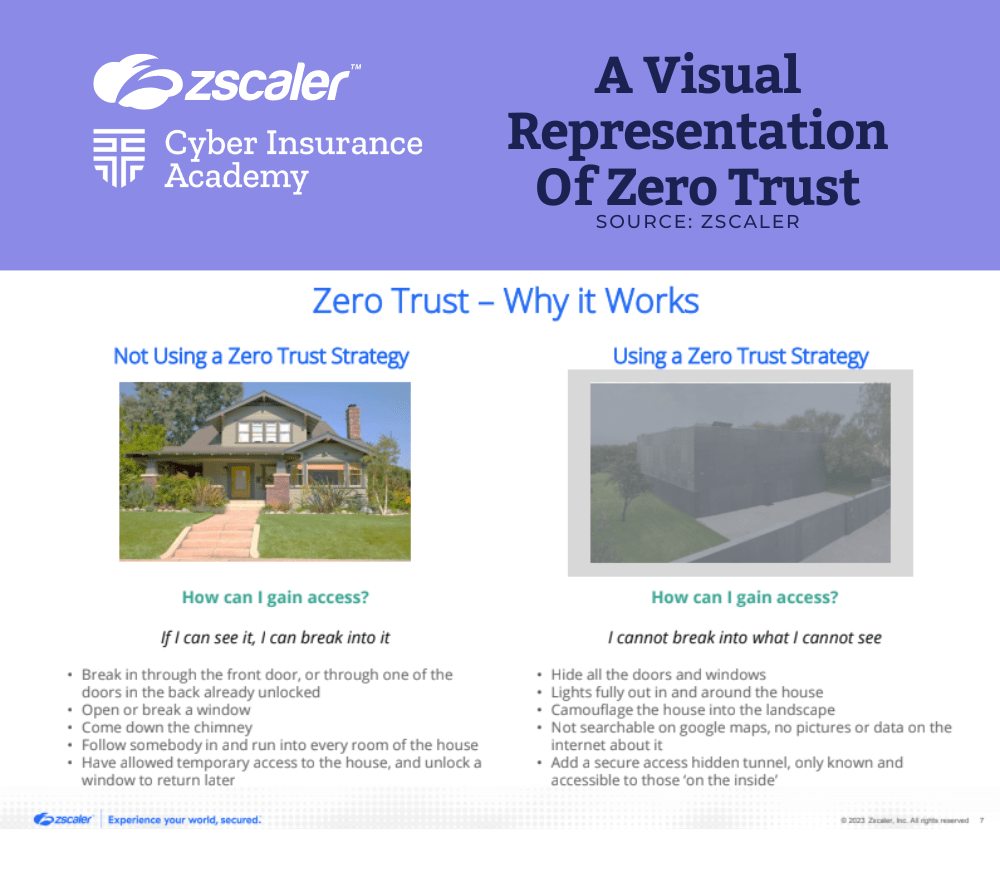
Overall, zero trust is a powerful tool that offers a proactive and comprehensive approach to cybersecurity, enabling organizations and insurers to protect their most valuable assets from potential harm. Need help visualizing the impact of a Zero Trust framework on your insured’s overall security hygiene?
Check out Stephen’s slide below for a simple visualization using a typical house as a metaphor:
Watch our Masterclass Recording
Check out a sneak peak of our Masterclass and download a full recording by filling in the form.
Stay tuned for Part 2 of our Zero Trust Masterclass Round Up, which will cover the the minimum cyber security controls needed to implement a comprehensive Zero Trust framework and will provide guidance on applying the framework to real-life proposal form questions.







