Backups are a critically important component to cyber incident response and recovery since properly implemented backups enable faster data restoration and mitigate the need for victims of ransomware to pay costly ransoms. In our recent Cyber Incident Response Masterclass, led by Joe Kingland at Blue Team Alpha, we learned about methods of securing data backups and best practices that your clients should be implementing today. This article summarizes the key points made by Joe, but to watch a full, on-demand recording of the IR Masterclass, fill in this form.
3 Strategies To Enhance Protection of Data Backups
In any modern business, data sits at the heart of what it does. It is often central to privacy regulations such as HIPAA, GDPR and CCPA. With regulators becoming increasingly stringent with data back-up compliance requirements, now is the time to check in with your insureds and clients and to make sure they are updated on the industry standards.
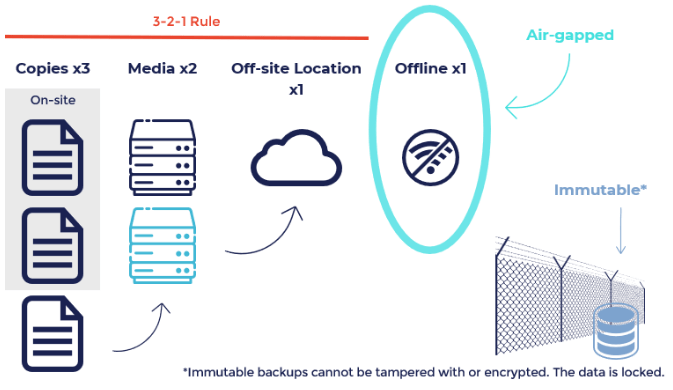
“3-2-1” Backups
The 3-2-1 strategy requires organizations to create and maintain three copies of their data on-site, including two live copies that replicate in case one system fails, ensuring availability on the second system. In addition, under this rule, data should be stored on two different types of media, such as hard drives, tape drives, or offline drives. This ensures redundancy and protects against media failures. Finally, the 3-2-1 Rule dictates that the copy of the data should be stored in an off-site location, typically in the cloud. This enables data restoration in the event of local infrastructure damage.
Offline Air-Gapped Backups
An air-gapped backup refers to keeping a copy of the data on a disconnected storage medium like tapes or unplugged hard drives. This ensures that attackers cannot access the data without physical intervention, providing an extra layer of protection.
Immutable Backups
An immutable backup refers to a backup that cannot be deleted or modified. They are usually stored in separate data repositories and are retained for a specific duration. For example, you might find that your clients make one backup per day and retain it for seven days. Immutable backups, even if online, offer strong protection against ransomware attacks as they cannot be tampered with or deleted.
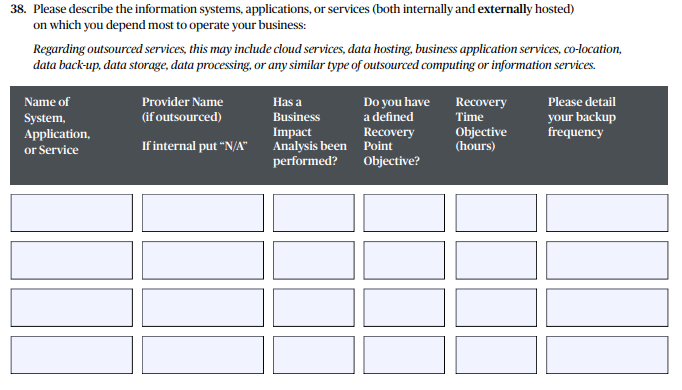
RPO and RTO Strategies
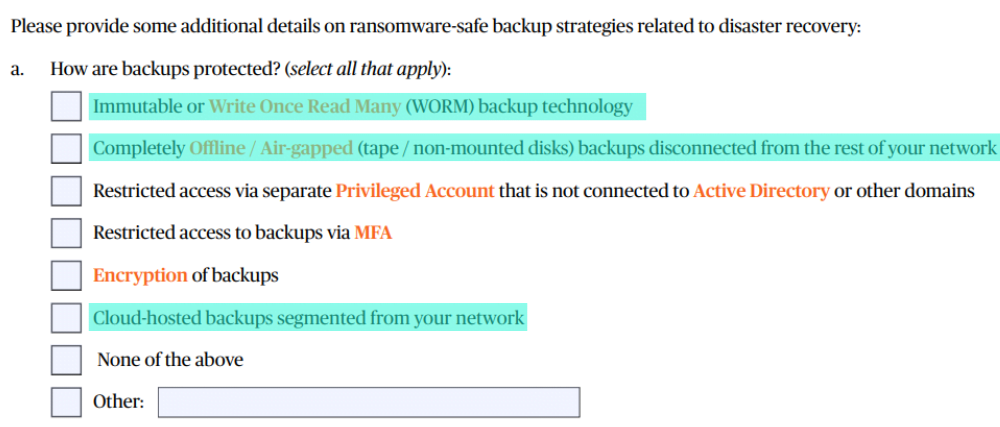
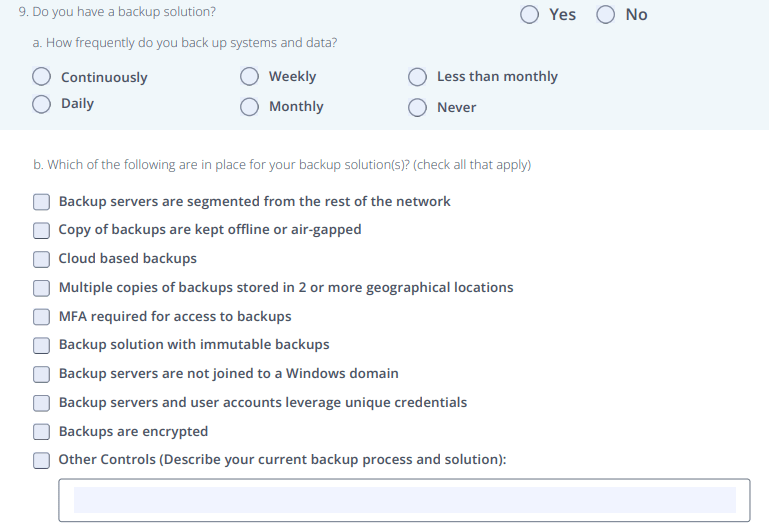
It is important for policyholders or those applying for a policy to conduct regular backup testing, to secure separate credentials (as well as MFA implementation), and to carefully consider the recovery time when utilizing cloud backups. Ensuring that your insureds have put these measures in place will enable them to effectively prepare for and respond to cyber incidents, ensuring a smoother recovery process and minimizing the impact on their business operations.
Policy application forms often ask for Recovery Point Objectives (RPO) and Recovery Time Objectives (RTO), but what do these actually mean? RPO determines how much data can potentially be lost in the event of a restoration, while RTO refers to the time it takes to recover and bring the data back online. Carriers want to assess these objects in order to determine the maximum extent of business interruption (BI) that their insureds may face in the event of a cyber incident. This realistic setting of expectations for business continuity ultimately dictates the premiums set by underwriters.
For example, although cloud backups are lauded for their off-site storage benefits, downloading large volumes of data from the cloud can be time-consuming, especially if insureds have on-premise servers and need to restore significant amounts of data. This means that the RTO from a cloud backup may be considerably greater. To address this, cyber insurance professionals should make sure that their insureds have explored alternative options, such as having the cloud service provider ship physical drives containing the data, which can expedite the restoration process.
Regularly testing backups to make sure that they function properly is also critically important for reducing RPO and RTO. By testing backups periodically, clients can ensure their effectiveness and identify any issues or gaps that may hinder data restoration in case of a cyber incident.
Clients should be able to demonstrate the infrastructure considerations that have shaped their backup policies. In the event of a ransomware attack or other cyber incidents, forensic analysis is essential to understand the attack and prevent future breaches. During this process, insureds also need to restore their infrastructure and bring their systems back online. To facilitate this, therefore, they should have a plan in place for a suitable location to restore their backups, ensuring that the forensic analysis can continue simultaneously with the restoration efforts. This requires having the necessary resources, such as computers and storage devices, readily available to restore backups efficiently.
Finally, using the same credentials for backup systems as those used for other network services carries great risk. If an attacker gains access to the network credentials, they can potentially delete or compromise the backups, rendering them useless for data restoration. To mitigate this risk, carriers will often check whether their insureds use separate credentials for their backup systems, ensuring that even if network credentials are compromised, the backups remain secure and intact.
RPO and RTO best practices
When assessing the RPO and RTO quoted by the insured, cyber insurance professionals should consider whether the following has been considered:
- Has the amount of data that the client can afford to lose been balanced against the impact it would have on their business? Answers for RTO should usually range from a day to one week, depending on the size and nature of the business.
- Has the client considered the cost of more frequent backups versus the risk of having to redo work if data is lost?
- Have options for spacing backups and achieving longer-term data retention been explored by the client?
Safeguarding data backups is essential in protecting organizations from the damaging effects of cyber incidents and is a crucial component of competent Incident Response (IR). Watch the full IR Masterclass for more guidance on best practices for building incident response plans and key relationships for insureds to establish ahead of a cyber incident.